Regula checks infrastructure as code templates (Terraform, CloudFormation, k8s manifests) for AWS, Azure, Google Cloud, and Kubernetes security and compliance using Open Policy, let’s dig in a bit deeper and see how we can make this integrate with Travis CI.
Regula + Travis CI
We’re gonna get Regula up and running, with something I thought of which is using a mock_key.json file I created, this is so you can sample it first, once you get a final main.tf (Terraform), you can edit as you please. Once Terraform calls Regula then Travis picks up the /POST and sees if it gets a response from Regula. This is a working example, and Travis is in my opinion the easiest development tool, to set Regula up on and get up and running with max uptime.
Terraform
We can grab Terraform by putting this in our script hook in our travis.yml file:
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
sudo apt-get update && sudo apt-get install terraformKubernetes
There is a compliant Kubernetes pod in this repo I’ve also banged out, since we’re using Travis there’s not alot of need for it, but I’m just trying to give you the most feasible option.
Swagger
There’s a full swagger.yaml file within the repository.
Travis CI
All of the .travis.yml file below was made by me (Montana Mendy). Just some crucial points to go over for the .travis.yml:
group: edge
branches:
only:
- master
- /^(cherry-pick-)?backport-\d+-to-/
addons:
apt:
packages:
- moreutils
env:
global:
- 'PATH="$HOME/.local/bin:$PATH"'
- REGULA_VERSION=1.6.0
install:
- >-
if [[ "${TRAVIS_COMMIT_MESSAGE}" = *"[Build latest]"* ]]; then export
BUILD_VERSION="$(cat packaging/version | cut -d'-' -f1,2 | sed -e
's/-/./g').latest"; fi;
before_script:
- mkdir "$HOME/.local/bin"
- >-
curl -L
"https://github.com/fugue/regula/releases/download/v${REGULA_VERSION}/regula_${REGULA_VERSION}_Linux_x86_64.tar.gz"
| tar -xvz -C "$HOME/.local/bin"
- 'RANGE1=`echo "$TRAVIS_COMMIT_RANGE" | awk ''{n=split($1,a,".");print a[1]}''`'
script:
- REGULA_OUTPUT="$(mktemp)"
- (regula run -f json || true) | tee "$REGULA_OUTPUT"
- REGULA_RULES_PASSED="$(jq -r '.summary.rule_results.PASS' "$REGULA_OUTPUT")"
- REGULA_RULES_FAILED="$(jq -r '.summary.rule_results.FAIL' "$REGULA_OUTPUT")"
- regula -v
- regula init
- regula run
- regula run --format table
- >-
echo "${REGULA_RULES_PASSED} rules passed, ${REGULA_RULES_FAILED} rules
failed" >&2
- 'if [[ "$REGULA_RULES_FAILED" -gt 0 ]]; then exit 1; fi'
- curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
- sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
- sudo apt-get update && sudo apt-get install terraform
- terraform -v
after_deploy:
- >-
if [ -n "${BUILDER_NAME}" ]; then rm -rf /home/${BUILDER_NAME}/* && echo
"Cleared /home/${BUILDER_NAME} directory" || echo "Failed to clean
/home/${BUILDER_NAME} directory"; fi;
- 'if [ -d "${PACKAGES_DIRECTORY}" ]; then rm -rf "${PACKAGES_DIRECTORY}"; fi;'
- >-
if: "((branch IN (master, develop) && type = push) OR branch =~ /.*env.*/ OR
commit_message =~ /\\[recreate env\\]/) AND commit_message !~ /\\[delete
env\\]/ AND type != cron AND commit_message !~ /\\[execute .*. test\\]/ AND
commit_message !~ /\\[start recreate scheduler\\]/"We are going to change the PATH and use cURL to fetch the latest version of Regula, make sure you have it by going to https://regula.dev/. You can also make sure by running:
regula versionIn the CLI, but it will print out something like this:
If the regula command isn’t working you need to install Regula and the binary. Make sure you run the following:
brew tap fugue/regulaOnce brew has symlinked fugue/regula, you can now start the install process:
brew install regulaIf you want to upgrade regula, just run:
brew upgrade regulaYou’ll also notice we used cURL to grab Terraform via:
script:
- curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
- sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
- sudo apt-get update && sudo apt-get install terraform
- terraform -vRunning Regula with a config file
You’ll want to pull up your CLI, make sure you have a directory named /infra_tf, and run:
regula run -f json --include example_custom_rule --include config.rego infra_tfThe output should be something like this:
{
"controls": [
"CIS-Kubernetes_v1.6.1_5.1.6"
],
"filepath": "pod-compliant.yaml",
"input_type": "k8s",
"provider": "kubernetes",
"resource_id": "Pod.default.hello",
"resource_type": "Pod",
"rule_description": "Service account 'automountServiceAccountToken' should be set to 'false'. Avoid automounting service account tokens. Service account tokens are used to authenticate requests from in-cluster processes to the Kubernetes API server. Many workloads do not need to communicate with the API server and hence should have automountServiceAccountToken set to false.",
"rule_id": "FG_R00484",
"rule_message": "",
"rule_name": "k8s_service_account_tokens",
"rule_result": "PASS",
"rule_severity": "Medium",
"rule_summary": "Service account 'automountServiceAccountToken' should be set to 'false'",
"source_location": [
{
"path": "pod-compliant.yaml",
"line": 1,
"column": 1
}
]
}
"summary": {
"filepaths": [
"pod-compliant.yaml"
],
"rule_results": {
"FAIL": 0,
"PASS": 14,
"WAIVED": 0
},
"severities": {
"Critical": 0,
"High": 0,
"Informational": 0,
"Low": 0,
"Medium": 0,
"Unknown": 0
}
}Depending on the policies, enforcements you’ve set it will look different. Now let’s make sure in Travis CI if our pods are compliant:
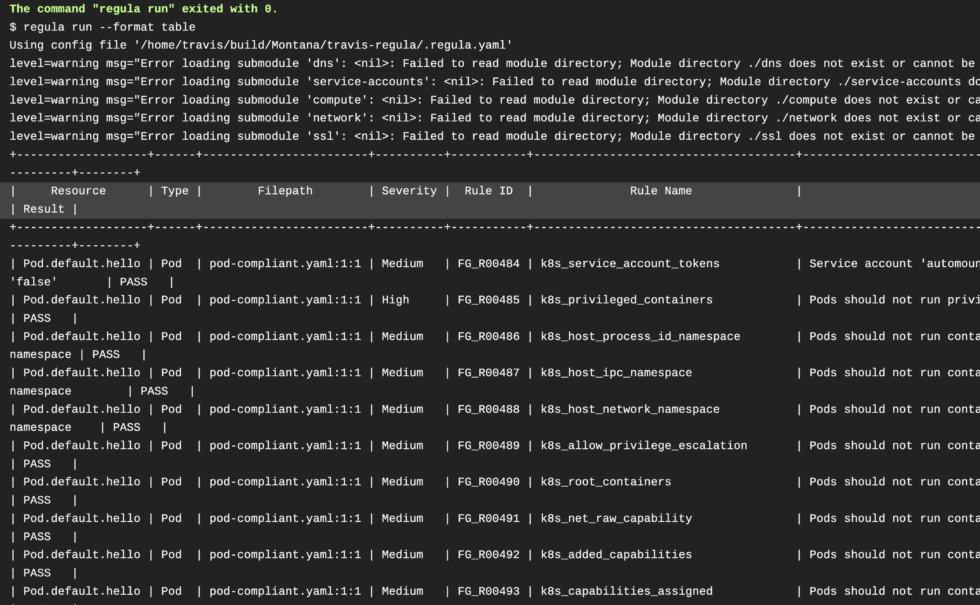
They certainly seem to be, now we can move on!
Usage
The usage does get pretty complex from the Regula side – I’ve been thinking about writing a bash script to help users and make it easier.
Conclusion
Here’s my repository for the integration, as always I try and make as much of my code as open source as possible. As always, if you have any questions, please email me at montana@travis-ci.org for help.
Happy building!