It’s a given that collaboration happens at multiple levels when building software in Git repositories. One popular way of collaborating is to ‘fork’ an original repository and execute a ‘pull request’ (PR) against the original (i.e., ‘base’) repository. Employing a CI/CD tool in this scenario usually takes place as an automated check to see whether the changes proposed in the pull request from the fork will break anything in the base. However, for this to work, the base repository must often share some secret data with the fork, which a malicious actor could abuse.
Some teams wish to accept the risks and share these secrets, while some do not. Regardless of what is the best decision for your organization, we believe you deserve a choice. This is why we are excited to introduce new repository-level settings in Travis CI that allow repository owners and administrators to explicitly make this choice.
For all repositories activated in Travis CI before March 1, 2022, the default repository-level settings will be as follows:
All repositories activated in Travis CI after March 1, 2022, will have both settings set to OFF by default – after this change, organizations that wish to enhance collaboration by working with ‘forks’ by sharing some of the ‘base’ secrets or SSH keys will be required to explicitly enable these settings at the repository level in Travis CI. This will allow teams to change repository access for fork settings to fit their specific needs. See figures 1 and 2 below that show these settings:
All repositories activated in Travis CI after March 1, 2022, will have both settings set to OFF by default – after this change, organizations that wish to enhance collaboration by working with ‘forks’ by sharing some of the ‘base’ secrets or SSH keys will be required to explicitly enable these settings at the repository level in Travis CI. This will allow teams to change repository access for fork settings to fit their specific needs. See figures 1 and 2 below that show these settings:
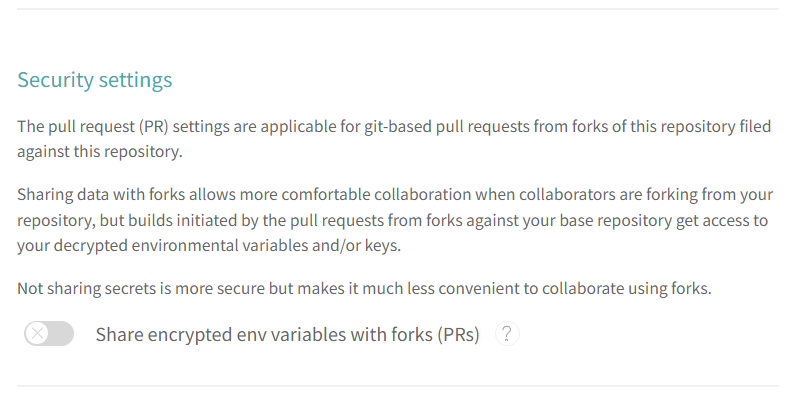
Fig. 1 Public repository settings in https://app.travis-ci.com
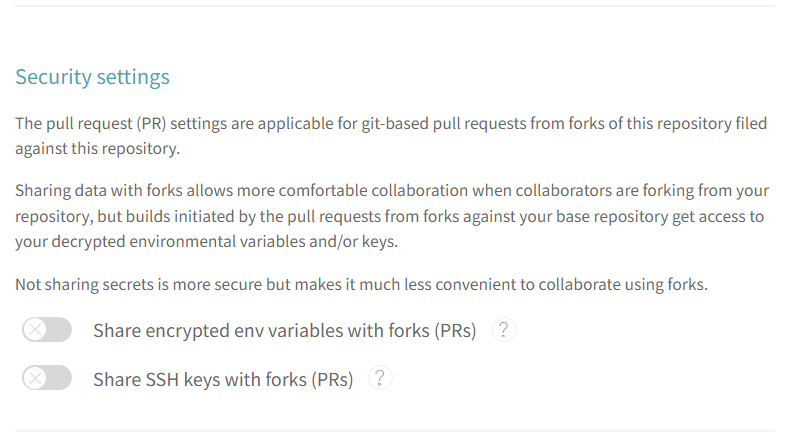
Fig. 2 Private repository settings in https://app.travis-ci.com
If you have repositories activated in travis-ci.com before March 1, 2022, and are working with pull requests from forks, then no changes are necessarily required. However, you may still adjust repository settings whenever you wish. Please be aware of the potential risks to public repositories if you choose to enable this setting. After March 1, 2022, if you wish to share encrypted secrets and/or SSH keys with forks in order to have pull requests from forks of a repository built as a part of your CI/CD procedures, you will need to adjust the repository-level settings. If you work with pull requests filed from branches of the repository instead of from forks, this change does not affect you.
The change is going to be released to:
The Travis team would like to use this occasion to say “Thank you!” to all the researchers and engineers contributing with their reports to enhance security here at Travis CI!
As always, if you have any questions, please email support@travis-ci.com for help.
Happy building!